5. Proof of Concept implementation
In order to verify our findings we implemented a PoC attack. For this PoC we envision an attack scenario where an adversary is nearby while the legitimate owner parks their car; the adversary now has a limited amount of time in order to clone the key fob and drive off.
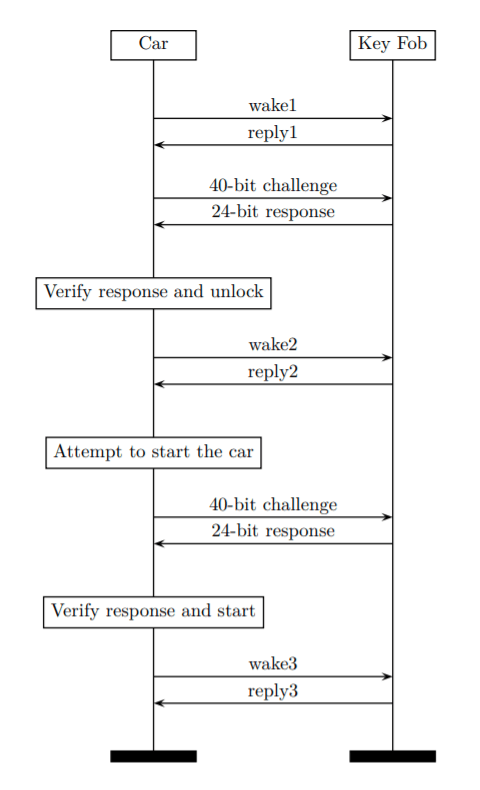
The attack will be carried out in three or four phases:
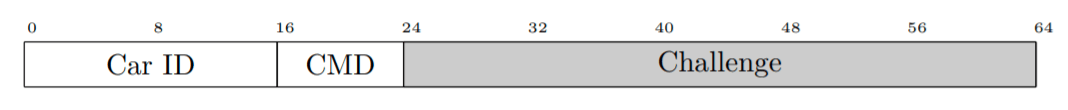
Phase 0: Receive car wake message (optional). As a first step, the attacker records one wake frame periodically transmitted by the car in order to learn the car identifier. This is an optional task since one could brute force the 2-byte identifier when in proximity of the victim’s key fob.
Phase 1: Car impersonation. During this phase, the adversary impersonates the victim’s car, transmits two chosen challenges to the victim’s key fob, and records the responses. During this phase the adversary would have to be relatively close (roughly 1 m) to the legitimate key fob for a few seconds (e.g. walking by the target) in order to acquire the two challenge-response pairs.
Phase 2: Key recovery. During the second phase the adversary recovers the 40-bit key from these two challenge-response pairs.
Phase 3: Key fob impersonation. After recovering the 40-bit key, the adversary proceeds to mimic the behavior of the victim’s key fob to unlock and start the target vehicle.
For Phases 1 and 3 of the proposed attack we made minor modifications to our protocol analyzer. Phase 1 is possible due to the lack of mutual authentication in the protocol. Our implementation of Phase 2 is now explained in detail.